OSINT on Signal is not an oxymoron – and it’s for good.
Secure messaging apps like Signal have become essential ways to protect ourselves from an intrusive world. End-to-end encryption and a staunch commitment to anonymity are exactly why Signal is a trusted platform for activists, journalists, and security-conscious users worldwide – for better or for worse. However, these same attributes make Open-Source Intelligence (OSINT) on Signal much more complicated.
Signal’s encryption is built to keep messages private, but even with the app’s watertight security features, metadata, public profiles, and digital footprints can still be revealed. With OSINT, it’s possible to gain insights into users, potential contacts, and even identify malicious actors. This is a corner of SOCMINT that offers powerful ways to enhance security — or, in the wrong hands, exploit it. In this article, we’ll explore how OSINT intersects with Signal, ethical boundaries, and how using it responsibly can enhance (not undermine) your privacy on this high-security message app.
What is Open-Source Intelligence (OSINT)?
If you’re looking for a recap: OSINT is Open-Source INTelligence. Collecting and analysing data from publicly accessible sources, an OSINT practitioner utilizes online platforms, social media platforms, media publications, public records, metadata, government reports and even eCommerce to get crucial intel. Those making use of OSINT include governments, law enforcement, journalists, researchers, data analysts, cybersecurity professionals and private sector companies – from Fortune-500 titans to family businesses.
The core principle of OSINT is reliance on only publicly accessible information.
(For more, including distinctions between different OSINT branches, check out our OSINT Basics article, ‘What is OSINT?’)
Why OSINT Matters for Signal Users
There are times when you might want to gather more information about the individuals or organizations you’re communicating with than Signal is willing to immediately provide. Here are common scenarios where OSINT can be ideal for investigations featuring Signal and Signal users:
- Verifying Unknown People: A potential business partner, a client, or just someone new in your network you don’t recognize; OSINT can help you confirm if the person you’re speaking with is who they claim to be. If a user’s phone number is linked to a public social media profile, you can use SOCMINT to cross-check and verify their identity.
- Screening Mystery Calls: Receiving messages or calls from unknown numbers can be disorienting – especially from unverified contacts. Using OSINT reverse phone lookup tools, gather information on the phone number’s owner, their company, and their social media presence.
- Detecting Fraud and Scams: Fraudsters, scammers and cybercriminals love secure messaging platforms like Signal too. With OSINT, you can investigate anybody for a history of fraudulent activity, or a match to a known scammer or criminal profile. This is great for businesses used to unsolicited inquiries, or individuals who suspect phishing on the horizon.
Tracking Digital Footprints: OSINT can trace a person’s digital footprint across multiple platforms – LinkedIn, Facebook, Twitter (X), and even the Golf app. By cross-referencing the phone number or other identifying information with online data (or using accurate, in-depth OSINT tools like OSINT Industries) you can uncover any Signal user’s job history, affiliations, and interests — providing more context for your conversations, and better knowledge of your chat partner.
How to Apply OSINT on Signal
Signal is one of the most secure messaging platforms out there. With end-to-end encryption, minimal metadata retention, and privacy-focused design principles to protect user communications, you might think Signal’s an OSINT-proof ecosystem. Luckily, this is far from the case.
Plenty of OSINT techniques yield actionable insights on Signal — for cybersecurity professionals assessing threats, investigators and law enforcement verifying identities, or users seeking to enhance their own operational security.
Signal’s encryption means you’ll need direct access to see message content. However, OSINT methodologies can analyze peripheral data points:
- Publicly linked identifiers (phone numbers, usernames, or connected social media profiles)
- Behavioral patterns (message timing, frequency, and network associations)
- Operational security (OpSec) oversights (i.e. lazy people reusing usernames across platforms, or not concealing their number)
Here’s some practical OSINT approaches to get at these points via Signal:
1. Phone Number Reverse Lookup
Even though Signal uses your phone number for account creation, the app no longer requires your number to be visible to everyone you chat with. Still, if you’ve got a listed phone number for your subject, you can use reverse phone lookup services to identify a name, location, and other publicly available details about the person linked to those digits – if you get an email or username, these make great selectors for new lookup searches. Try:
- TrueCaller: A widely used app and service that identifies unknown calls. It provides data like the name, location, and even whether the number has been flagged as spam.
- OSINT Industries – A 100% accuracy-guaranteed, real-time OSINT search platform that allows you to reverse search phone numbers, emails and usernames across 1000 platform modules and growing.
- Maltego – A data mining and link analysis tool, Maltego allows investigators to map connections visually. Alternatives for graph visualization like this include Spiderfoot and OSINT Industries Palette.
While these tools won’t directly link to Signal accounts, they can help you gather information about who is contacting you based on the phone number you’ve verified is theirs. It’s also important to note phone numbers are no longer shown on Signal thanks to the introduction of usernames; most people reuse these across platforms, so some tools like OSINT Industries offer username search to get your search going anyway.
2. Social Media Cross-Referencing
After (or before) your search on an OSINT tool, you can investigate a Signal contact with simple SOCMINT. By cross-referencing the information you find on social media profiles through lookups or other investigation techniques.
- LinkedIn: Almost all professionals today use LinkedIn to share their career history and affiliations. If you have a name or company you know links to a phone number, check LinkedIn. Here you can often confirm their identity – and more about their professional life and past.
- Facebook and Twitter: If your subject uses Facebook or Twitter (X), use these to uncover additional details. These accounts can show you more about your subject than just who’s on their Friends or Followers lists.
- Instagram: Visual-based platforms can illuminate someone's lifestyle, interests and personal brand in a way text-based platforms like Signal can’t. If you find a presence on Insta, Flickr, Tumblr or even TikTok, use this information to put a face to a name.
Social media profiles don’t always directly correlate with Signal accounts, but by piecing together information from multiple platforms, OSINT tools can help you to identify and understand Signal. Be aware, this kind of SOCMINT can take time!
3. Analyzing Digital Footprints
Beyond reverse lookups, OSINT also allows you to dig deeper into a person’s digital presence. This includes blog posts, comments, articles and public contributions they may have made online.
Try Google Dorking. Search engine hacking techniques can find hard-to-reach information about a Signal user with just the search engines we all use every day. By crafting complex and targeted search queries, you can get to the good stuff: personal blogs, professional directories, and even publicly exposed artifacts (group invites, leaked docs, or metadata) from Signal itself. Try these basic operators:
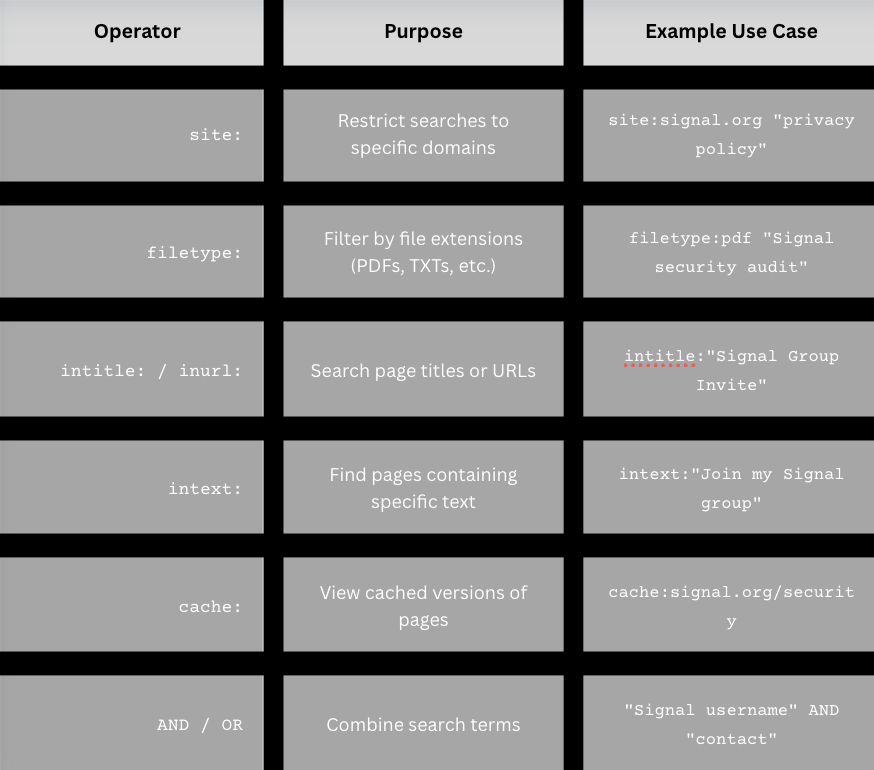
You can also try specific Google dorking operators for Signal OSINT. These will make sure to tailor your searches to the platform you're hoping to investigate.
To find Public Group invites:
intext:"signal.group" OR "signal.me"
intitle:"Signal Group" OR "Join my Signal"
To locate public Signal-related documents:
filetype:pdf "Signal protocol" OR "Signal encryption"
To see forum discussions about Signal:
site:reddit.com "Signal username" OR "Signal burner number"
site:twitter.com "My Signal ID is"
To identify publicly-shared phone numbers:
intext:"Contact me on Signal" +1 (XXX) XXX-XXXX
It’s important to note these operators only dig up publicly posted data, not encrypted content itself, adhering to the basic principle of OSINT. Try combining operators for more niche results, like:
site:twitter.com intitle:"Signal" (intext:DM OR intext:message)
(An OpSec Tip – use a VPN/VPS when testing these queries to avoid exposing your own IP in sensitive investigations.)
Ethical Considerations in Signal OSINT
By piecing together all the information you gather through OSINT, you can verify whether someone is worth engaging with on Signal. But while OSINT is (obviously) incredibly useful, it’s powerful too. OSINT tools and techniques are made to be used responsibly; the goal of OSINT is to gather intel without putting anyone's privacy in jeopardy. Always:
- Respect Privacy: Never engage in anything close to harassment or stalking. Try not to come into further contact with your subject while investigating.
- Be Transparent: If you gather information, especially for law enforcement or business purposes, be transparent about your intentions. Deliver your concise and comprehensive report to the relevant authorities, as soon as possible.
- Comply with the Law: Read up on relevant laws, especially when it comes to data privacy regulations – we mean GDPR or CCPA. Use OSINT tools with sound ethics and compliance policies.
To see OSINT on encrypted platforms in action, check out our Case Studies.
“I simply cannot look away…”
Read: Avenging Angel: An OSINT Activist Fighting 764 Sextortion and O9A


