Try the world's most popular OSINT platform for free. Elevate your enterprise investigations with unmatched accuracy.
In a so-called “safe space” for teens, @akaclandestine finds the adult in the room.
“Never ever ever ever let your child on there, full of groomers and pedos… no matter how safe they claim it is, and how much they say they moderate, THEY DO NOT CARE ABOUT THE SAFETY OF YOUR CHILD.” – A Redditor discussing ‘kidschat’ on r/parenting. [Source: Reddit/OSINT Industries]
Online chatroom kidschat.net claims to offer “free chat rooms for older kids and younger teens", restricted to those “a minimum age of 13” who can get “a parent’s permission”. Likewise, teen-chat.org claims to be “the #1 source for free chat for older kids", with the same misspelled statements forbidding users over the age of nineteen.
Kids themselves sum it up better. As one teen Redditor summarized on r/creepyPMs: “Yeah that site is mostly pedophiles. I'd stay away from it.”
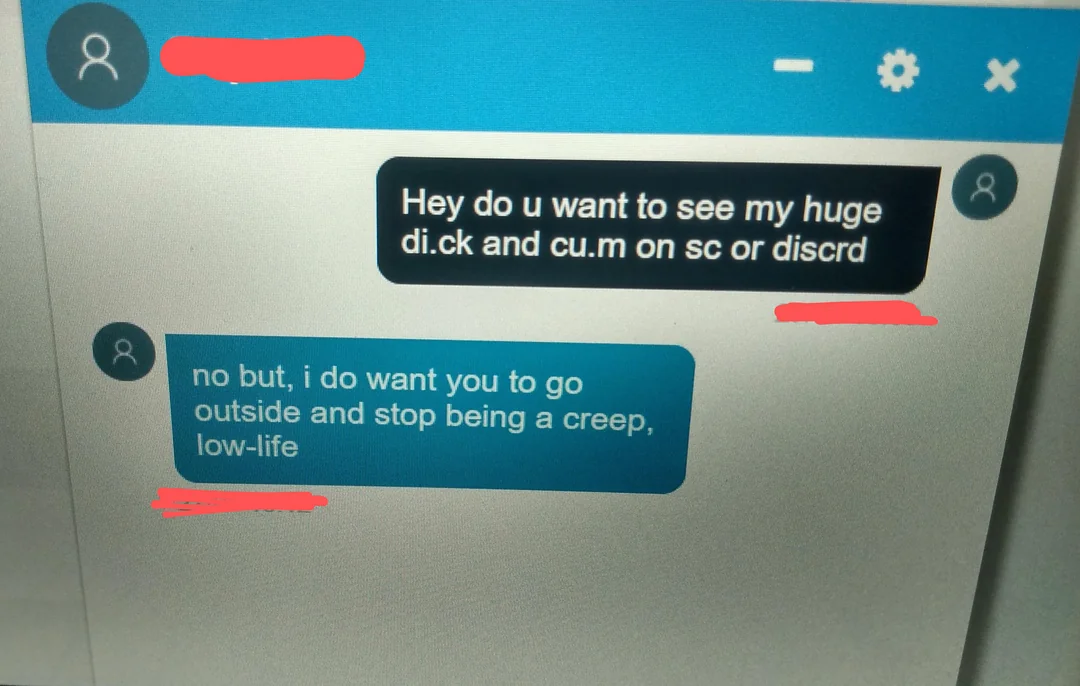
As far as functionality goes, kidschat and teen-chat are generic identikit sites, barely developed beyond a basic template. They’re also two of the internet’s most notorious free predator chatrooms. The first results on Google for the queries ‘kids chatroom’ and ‘teen chatroom’ respectively, they’ve been receiving consistent traffic since the turn of the century. Even though the chat is not for “dating or matchmaking”, LGBT teens are asked to “please” go to their respective chatrooms instead; here they’ll see even fewer rules about keeping content “appropriate and clean… for regular boys and girls”.
“Someone tried to bait me into killing myself on Kidschat.net, in the middle of the pride fall thing. He sent rape threats because I said no and started spamming me religious stuff… how God hates me.” – A teen Redditor discussing a ‘sketchy website’ on r/ask. [Source: Reddit/OSINT Industries]
The claims to be ‘kids-only’ fall apart seconds after logging in. It’s normal to see ‘hundreds’ of predators, and whether this is exaggeration doesn’t erase the immediate messages in your inbox. Reporters from Melbourne’s Herald Sun found contrary to the sites’ claims of no "matchmaking", even the younger-oriented kidschat includes themed areas like ‘flirt room’, ‘role-playing room’, and ‘find ur true love’. Posing as an 11-year-old girl, the reporters received a deluge of messages from adults in their late 20s to early 40s – soliciting nude images, video calls, and meetups. One read, “Do you want to watch me naked on camera with your mother?”
Even from a cursory browse of discussions, kids are clearly aware that these sites are ‘sketchy’. But where are the grownups?
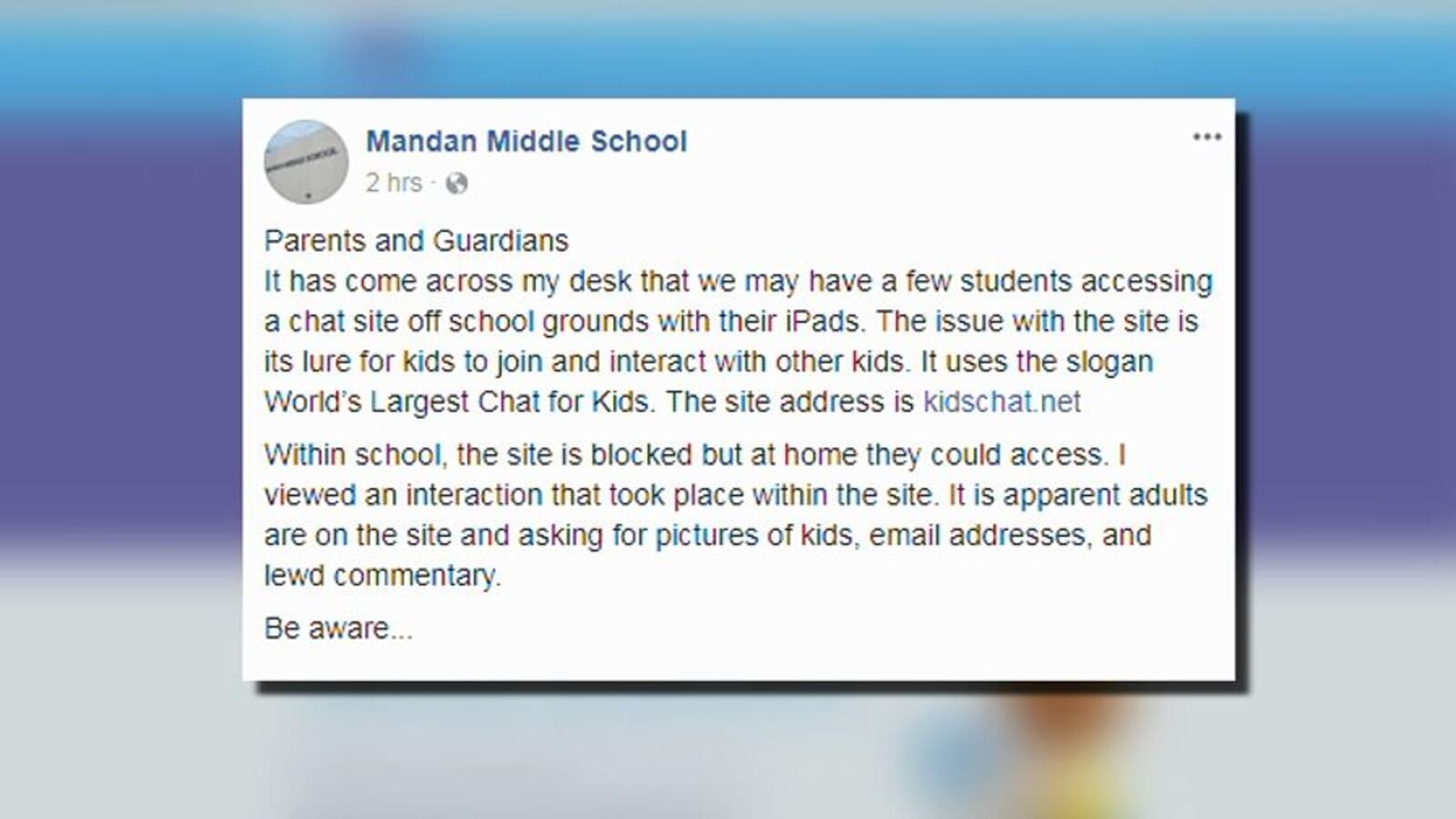
Some Redditors cited experiences as far back as 2005. In 2018, small North Dakotan secondary Mandan Middle School issued a parent alert about kidschat. In December 2019, Ohio’s City of Westlake Police Department issued a public alert on Facebook: "be on the lookout for the website teen-chat.org". Las Vegas PD concurred, identifying teen-chat as a "dangerous teen chat website". By 2020, both sites and sister site Chat Avenue had been covered by YouTubers MamaMax and Nexpo, names swiftly banned by both sites’ filters. A "Take down KidsChat.net" petition began on Change.org. Last year, the Australian Federal Police and the eSafety Commissioner issued a 2024 warning in response to the Herald Sun investigation that year.
By now, kidschat – formerly known as ‘ChildrensChat’ – had come of age itself, passing its eighteenth birthday.

Vague safety advice about parental supervision only exists to shift blame. These sites have no moderation beyond simple filters, and encourage users to report those ‘acting’ older than 19 or younger than 13. The report button often leads to a 404 error.
“I used to go on the teen version… both need to be taken down. I saw many many older men trying to talk to teens who were 13-17… Had a few times where someone would come into the chat and blast porn, beastiality [sic] and other fucked up videos/pictures. The mods would remove them as soon as but there was a few times this took several minutes exposing kids to literal horse porn.” – A Redditor discussing the ‘sketchy websites’ on r/RBI. [Source: Reddit/OSINT Industries]
According to the supplied staff lists on kidschat, the mods are largely ‘teens’ themselves; on teenchat, a (mostly unconvincing) piece on increased safety measures lists one name that crosses over on both Admin lists, as part of a transitional addition to the ‘teenchat.org team’ in 2023 – Arkham. Requesting to join the (mostly teenage) mod team required emailing Arhkam. Nevertheless, other mods and admins insisted he was not the site’s owner, or the man in charge. He did, however, read messages both in the ‘main chat’ and private.
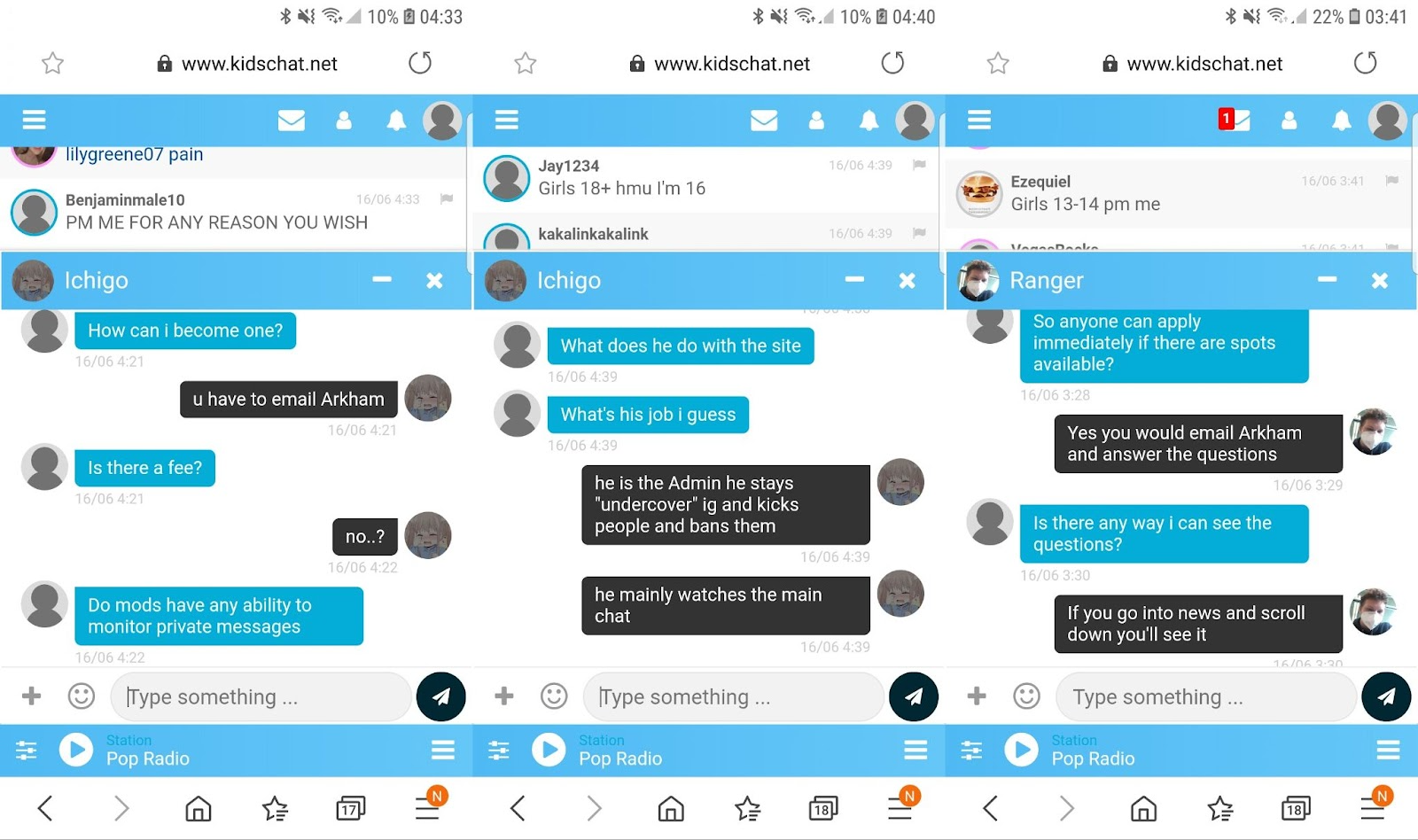
Meanwhile, discussion of the "sketchy websites" continued on forums like Reddit and Discord. Here, the owner’s name was common knowledge among teenage ex-chat users.
“I am legitimately curious, how is the website kidschat.net still able to continue running? Can police not literally type that link into the address bar and watch crimes being committed before their eyes?”
"the owner is from Canada
his name is Daniel Yee,
he hosts the site on Cloudflare
he buys servers in the USA, but lives in Canada as a way to A. not get caught
and B. not get arrested
so, to take down the site, you'd need to contact Canadian police about it" – Redditors discussing ‘kidschat’ on r/NoStupidQuestions. [Source: Reddit/OSINT Industries]
The Target: Daniel Yee, a.k.a. ‘Arkham’
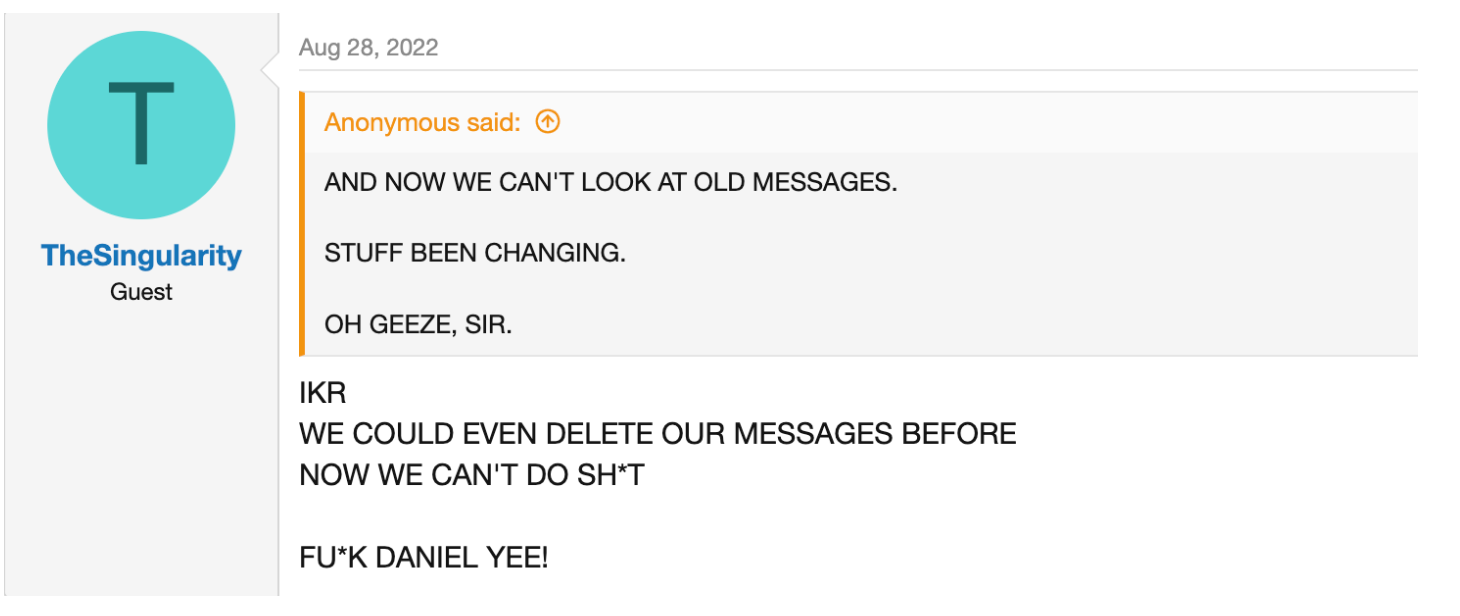
In August 2022, frustration was boiling over on kidschat and teen-chat. Disgruntled users were taking to public forums to vent about decisions made by the sites’ administrator. A controversial change to the platforms’ message deletion policies had led to a revolt, with a clear rallying cry. Users were spamming a chant: “FU*K DANIEL YEE!”
Not only were users openly naming him, but they were posting his operational emails, domains and personal details. By doxxing Daniel Yee, chat site users were demanding accountability.
@akaclandestine is a world class OSINT investigator, specialising in security, OpSec, Humint, infosec, threat research and intelligence. His outstanding work has landed his name in the Cert-Eu, Gruppo TIM, Utrecht University, Basf, Bosch, Vivaldi, Philips, Bayer and UNESCO Halls of Fame.
His latest mission? To expose the predator site admin ‘Arkham’, or Daniel Yee.
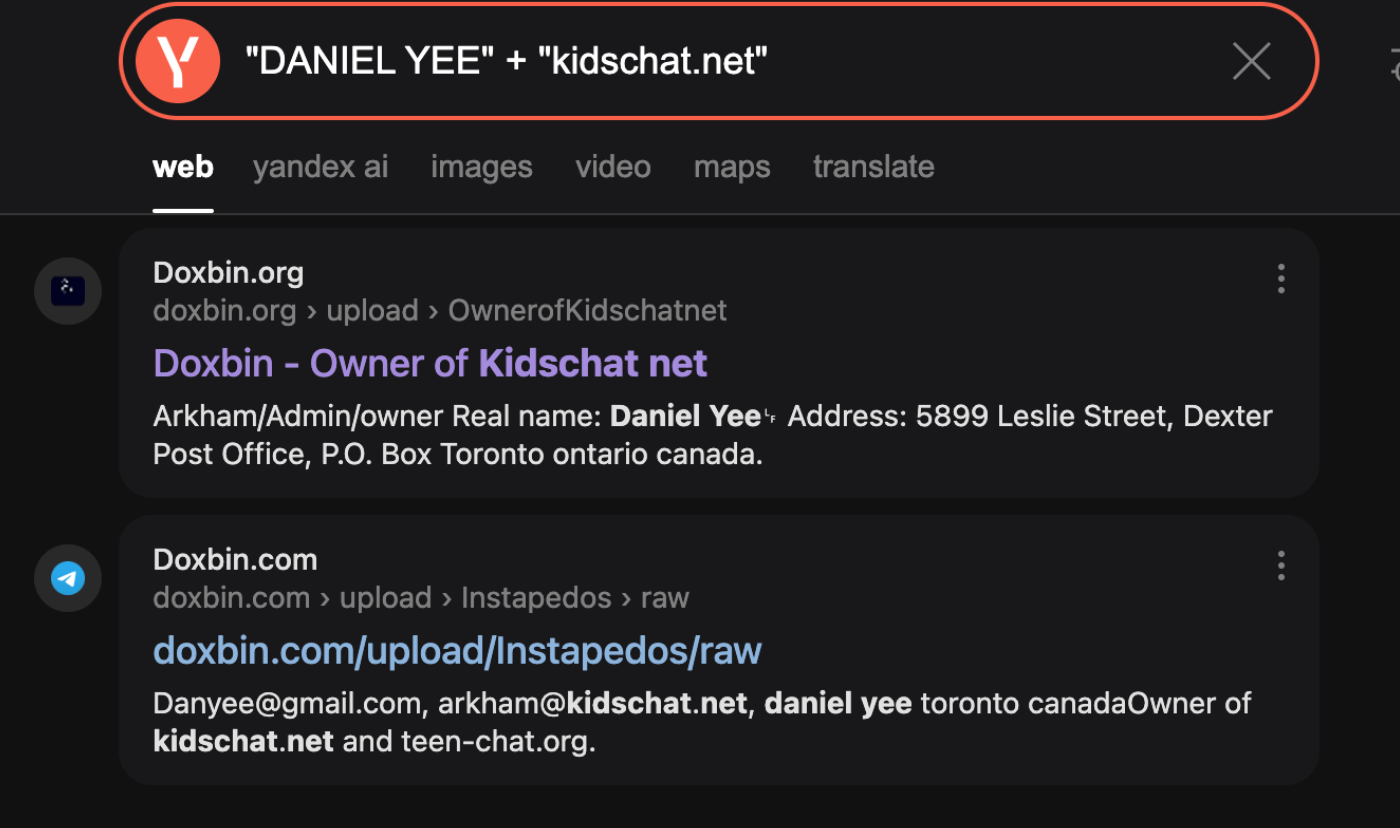
Taking advantage of the “F*CK DANIEL YEE” movement, @akaclandestine turned to Yandex, a more effective search method than Google for censored content. A quick dork uncovered Doxbin entries, featuring all the data needed to get started.
Full Name: Daniel Yee
Primary Email: danyee@gmail.com
Location: Toronto, Ontario, Canada
Associated Address: Leslie Street, Dexter Post Office, P.O. Box Toronto
Personal Domain: danyee.com
Operational Aliases: Dan Dan, D D, Dan Y., Vida Blue, Arkham
So begins an OSINT-powered masterclass in hunting a pedophile.
First Steps: From Doxbin to OSINT Industries
Doxbin provided an email address, and @akaclandestine is an OSINT Industries user. He knew that with our tool, the danyee@gmail.com address was a game-changer. An OSINT Industries search on this email delivered not just 25+ platforms worth of activity, but over 20 years of digital trail.
Microsoft and Google accounts tied to the address seemed to be Yee’s primary accounts. Unsurprisingly, the location data didn’t track with Doxbin.
ID: 1110*************6382
Name: D D
Last Activity: August 5, 2025
Microsoft (Main Account):
ID: FE14*********3EBF
Name: Dan Dan
Email Hint: da***@danyee.com
Created: December 13, 2005
Last Activity: August 7, 2025
Declared Location: CN (China) - Suspected OBFUSCATION
To such a seasoned investigator, this was an obvious obfuscation attempt. Among accounts that directly identified their owner, Yee used multiple locations and aliases to deliberately complicate his digital identity: ‘Vida Blue’, ‘TDotDan’, and the famous ‘Arkham’.
Quora (Obfuscation Attempt):
Name: Vida Blue - FAKE IDENTITY
Location: Cairns, Queensland, Australia - FALSE LOCATION
Created: January 11, 2014
Gravatar (Direct Identification):
Username: danyee358024847 - NAME+SURNAME COMBINATION
What’s more, OSINT Industries revealed activity on gaming platforms, web development tools and adult sites. To @akaclandestine, the former suggested contact with young people and the capability to build a basic site like kidschat or teen-chat. The latter indicated interests in line with predatory behavior.
Activision, EA, Call of Duty: Multiple gaming accounts
Analysis: Potential vectors for contact with younger demographics
Adobe, Autodesk, WordPress: Professional tools
Analysis: Capabilities for website development and content creation
XVideos:
Status: Registered
Analysis: Indicative of specific interests relevant to predator profiling
OSINT Industries was beginning to flesh out @akaclandestine’s digital predator profile. Our WHOXY module delivered the final blow connecting Yee to the two predator forums, listing his operational domains as follows:
danyee.com - Personal domain (linked to Microsoft account)
kidschat.net - Primary site targeting "older kids and younger teens"
teen-chat.org - Secondary site for "older kids and teens"
Still, perhaps the most damning evidence came from breach data @akaclandestine could acquire via OSINT Industries’ HaveIBeenPwned module. The danyee@gmail.com address appeared in 18 major leaks between 2012 and 2024. @akaclandestine painstakingly summarized the impact of each breach on his hunt.
Collection #1 (2019):
Scale: 773 million unique emails
Data: Email/password combinations for credential stuffing
Hunting Impact: CRITICAL - enables account takeover attacks
Gravatar (2020):
Data: Username "danyee" cracked
Hunting Impact: CRITICAL - direct correlation to real name
Neiman Marcus (2024):
Data: Email, name, phone, address, partial card data
Hunting Impact: Recent personal data exposure
On a complete breach timeline, the danyee address appeared in a decade of breaches:
- Dropbox (2012-07-01) - Initial compromise
- Disqus (2012-07-01) - Forum data
- vBulletin (2015-11-03) - Technical forums
- Lifeboat (2016-01-01) - Minecraft accounts
- Staminus (2016-03-11) - Hosting provider
- Exploit.In (2016-10-13) - Credential stuffing
- ShareThis (2018-07-09) - Social sharing
- Houzz (2018-05-23) - Home design
- Apollo (2018-07-23) - Professional data
- 2,844 Separate Data Breaches (2018-02-19) - Mass collection
- Collection # (2019-01-07) - Mass credential stuffing
- Zynga (2019-09-01) - Gaming data
- MGM Resorts (2019-07-25) - Hotel guest data
- Wattpad (2020-06-29) - Reading platform
- Gravatar (2020-10-03) - Username correlation
- Shopper+ (2020-09-14) - Shopping data
- Naz.API (2023-09-20) - Credential stuffing
- Neiman Marcus (2024-04-14) - Recent personal data
Why? Because Yee’s OpSec failures were glaring. The sheer number of exposures suggested to @akaclandestine’s expert eye a pattern across both personal and ‘business’ accounts. Yee was relying on a single Gmail account, repeating usernames (that often featured his government name) and had totally failed to contain the “F*CK DANIEL YEE” revolt – despite running the site on which it began. As a result, Yee’s digital identity was trivial to track and compromise. Obfuscation attempts suggested that Yee knew what he was doing needed to be concealed. Daniel Yee was not only running a pair of pedophile havens, but he was very bad at hiding it.
This is why, @akaclandestine concluded, Yee’s identity had become “essentially an open secret”. Now to catch him.
The Location: Where in the World is Daniel Yee?
Dan Yee made the most effort to hide his location. He “buys servers in the USA, but lives in Canada”; this way, in the words of a wise Redditor, he can “A. not get caught and B. not get arrested”.
What @akaclandestine needed was location verification. Yee claimed to exist all over the world, at times in China, at times in Australia. Doxed details placed him somewhere more mundane. Leslie Street, North York, Toronto: a grey north–south arterial road, home to such sights as the Leslie Street Spit, an Important Bird Area, and the Old Cummer GO Station.
Time to turn back to OSINT Industries. Among the results was a Yelp account.
Yelp (Real Location):
ID: rAdjz******yYzA
Name: Dan Y.
Location: Toronto, ON, Canada
Created: July 20, 2015
On this Yelp account, Daniel Yee had left several reviews in the Toronto area. The creator of the Internet’s two largest ‘sketchy’ chat sites left a review for Shoppers Drug Mart in Pickle Barrel Plaza – on Leslie Street, North York. There was also more to the “TDotDan” alias on his Plex account; the “T” could easily refer to Toronto, the “Dan” to Yee’s real name. When cross-referenced against these results and Toronto IP data, the obfuscating location claims quickly collapsed.
It was easy to undermine Yee’s Cloudflare strategy too. As confirmed by those watching on Reddit, the anti-prosecution technical configuration the predator sitemaster had created relied on hosting the site on a Cloudflare server based in the US. The administrative email, however, was “arkham@kidschat.net": an email confirmed, via OSINT Industries, to be Yee’s.
The strategy Daniel Yee hoped would protect him from the consequences of his actions was not only exposed by OSINT, but compromised. The international angle had been eliminated.
‘Arkham’ might route his servers abroad, but Daniel Yee’s physical presence in Toronto meant he was accessible to Canadian law enforcement. He was vulnerable, at last, to cross-border cooperation with the U.S.
OSINT Predator Hunting: The OpSec Failures That Gave Him Away
Predators may not actually be getting smarter.
Over 300 million young people experienced non-consensual sexual talk, texting, questions, requests or exposure to sexual images online in the past year. Cases occur at a rate of 10 per second. However, the one in nine men that admit online sexual offending against children are not all – as the cliche goes – becoming tech-savvier by the minute. Investigations like @akaclandestine’s prove it.
This OSINT predator hunt was “an unqualified success.” Yee’s identity, infrastructure, and location were brought to light, so Arkham could finally be brought to justice. Most crucially, however, this investigation showed a predator making 20 years of glaring OpSec mistakes.
The average age of online predators surveyed by the FBI’s Behavioral Analysis Unit was thirty eight. Although younger perpetrators are making the news, more mature (and less tech-savvy) predators have often been making slip-ups like Yee’s for most of their digital lives. With tools like OSINT Industries, these common vulnerabilities become a weight of cumulative evidence. When one search can scan the whole web, every mistake is permanent and exploitable.
Arkham’s groan-worthy OpSec flaws were obvious to digital-native teens. By calling Yee out, they inspired grownups with the tools to act. Here, @akaclandestine presents an OSINT-led model of predator hunting that blends community power with the precision of automated OSINT tools like OSINT Industries. While sites like kidschat and teen-chat slip blunt instrument safety legislation like the UK’s Online Safety Act - remaining accessible - OSINT is laser-focussed.
OSINT can find plain-sight predators before they find their prey.
“When we first started talking, he was totally normal, and we were just friends… By the time you feel endangered by a groomer, you feel like they already have too much on you.” – Jessica Walker, student and online grooming survivor. [Source: New York Post]
To find out more about @akaclandestine's work, visit his Twitter (X).
Start your free enterprise trial
Get Free TrialReveal what's behind any contact, instantly.
We want to hear your story!
Inspire Others
Educate about what OSINT can do.
Positive Publicity
Share your success with the world.
Support #OSINT4Good
Be part of the OSINT story.



